-
FAQs & Trouble Shootings
01. Host Configuration Guide For vCloudPoint's Shared Computing solutionView Host Configuration Guide For vCloudPoint’s Shared Computing solution in xls file. For support on a typical deployment, please contact our support team.
02. Windows Multi-user Licensing(Last update: 24-Mar-2016)
To properly license vCloudPoint zero clients in a Microsoft environment, certain CALs are needed for each vCloudPoint seat, along with certain OSes running on the host computer. Regarding the host machine, you have the option of running supported edition of Server 2008R2, Server 2012, Server 2012R2, Multipoint Server 2011, or MultiPoint Server 2012. Windows 7, 8, 8.1 and 10 will work with the vCloudPoint Sharing Computing solution but at this time cannot be shared under Microsoft compliancy. In order for the vCloudPoint workstations to be fully licensed, they will each need a Remote Desktop Services Client Access License (RDS CAL) along with a Windows Server Client Access License (WS CAL). The total cost of these CALs combined will range anywhere from $10-$120 per seat depending on the type of organization deploying the workstations, and their licensing agreement with Microsoft. But these CALs are perpetual licenses – not annual subscriptions.
The result of the licensing model differences by using the sharing computing , traditional desktop PCs and VDI over three years can be seen in the following example:
Sharing: One server OS license per target server ($883) + For each client device: ( 1 Server device CAL ($30) and 1 RDS device CAL ($102)) x 30 = $132 x 30 = $4,843
Desktop PCs: 30 target desktop OS licenses ($187 each) x 30 = $5,610
VDI: 30 target desktop OS licenses ($187 each) x 30 + For each client device: VDA rights subscription ($100 / device / year) x 30 devices x 3 years = $14,610
* Cost based on 30 thin clients (not eligible for SA) over 3 years, Windows Server 2012 R2 standard, Windows 8.1 Pro, US MOL pricing, corporate customers.
Things to consider:
-
- If you are replacing PCs, you may already have the WS CAL for each seat.
- If you are replacing thin clients, you may already have both the RDS and WS CALs.
While deploying zero clients from vCloudPoint, the required licenses mentioned above must be purchased from Microsoft Windows. It is significant to note that Microsoft’s license policy varies between countries and vCloudPoint users are requested to refer to their local Microsoft’s partners before purchase.
For further details on Microsoft’s multi-user licensing please refer to Microsoft’s website or licensing brief titled: “Licensing Windows Client Operating Systems in Multiuser Scenarios“.
03. Using Windows Active Directory (Domain) with vCloudPoint Shared Computing(Last update: 14-May-2016)
1, Your domain system should include at least one Domain Controller and one shared host that has joined the domain system. (DC uses static IP address–>install Active Directory Service from the DC’s Server Manager console–> create the domain–> shared hosts join the domain and point DNS to the DC’s IP address.)
2, Install the vMatrix Server Manager on the shared host(s).
3, Create users on the Domain Controller.
4, Add the domain users to the Remote Desktop Users Group on the shared hosts.
5, Log into the host with vCloudPoint zero clients. Hosts will automatically be recognized if they have joined the domain. The picture below shows two login options: the first domain name “CLOUDPOINT” is chosen for domain login; the second one “Local Account” is for local account login. If users choose local account login, they are logging on the host rather than the domain.
6, Select a domain, and then enter your username and password.
IMPORTANT NOTE:
1, You cannot log in an domain administrator account from a zero client. This will cause unavailability of the whole vMatrix and zero client system. If you mistakenly do this, remove administrators from vMatirxServerRemoteUsers group on the shared hosts thought Computer Management –> Local users & groups –> groups–> vMatirxServerRemoteUsers group
2, Doman NTLM is not support at the moment
Note:
1. By default, only users in the Administrator Group can log into the remote Domain Controller, users in the Remote Desktop User Group cannot.
2. If you are using a vMatrix version of 1.6.0.4 or earlier, you have to install the vMatrix both on the Domain Controller and Hosts. If you do not want to install vMatrix on Domain Controller, please use vMatrix version of 1.6.0.5 or later.
04. Zero clients get disconnected every a few minutes (Using zero clients without internet connectivity)(Last update: 09-Sep-2016)
By factory default, vCloudPoint zero clients and vMatrix Server Manager software are configured to be used in an internet connected environment (WAN). If your host is provided with internet, no additional configuration is required to be done. The Operation Mode displayed on the User Management page of any device connecting to the host will automatically change from “Offline” in red to “Online” in black, meaning the device is properly working in an internet provided environment.


However, if the Operation Mode of the devices connecting to the host stays “Offline” in red all the time, you have to re-configure the devices for offline usage, otherwise the devices may be disconnected every few minutes during operation. Use cases where you may encounter this problem and need to apply for “Offline Usage” normally includes the followings:
- you do not provide internet connection (WAN) to the host or the internet connection is extremely unreliable;
- you use proxy or VPN or internet control software that the host cannot access our configuration server: api.cpterm.com.
How to re-configure the devices for offline usage:
1) In a non-internet connection environment, vMatrix Server Manager will prompt a message window for offline usage configuration within 5 minutes after host boot.

2) Open vMatrix Server Manager, go to Offline Usage page (this page only appears when the host is not provided with internet connection on system boot).

3) Export the configuration profile. Before exporting, please connect all client devices for offline usage to the host, so that the serial numbers (SNs) will be collected in the file. Alternatively, you can write down the SNs if you cannot connect all the client devices (especially in large deployments). The host profile contains hardware information of the host. Therefore, make sure the host hardware, e.g., CPU, memory, drives and network card, are exactly the same as your real offline usage condition, otherwise, if there is any change to the host hardware, the final generated offline configuration will be invalid to the host.
4) The dealer will return you with a configuration file based on your last exported profile. Import the returned file to complete.
5) If your configuration for offline usage is successfully accomplished, the Operation Mode changes from “Offline” in red to “Offline” in black.
Note: Offline usage configuration on vMatrix Server Manager was introduced in the release of vMatirx Server Manager 2.0.2 version, if you are planning to use the vCloudPoint zero clients in a non-internent or unstable internet environment, please use 2.0.2 or a later version of vMatrix Server Manager, and contact the dealer for generating an offline configuration file.
05. Host is not shown in the host list at the zero client's login menu.(Last update: 23-May-2016)
1) The vMatrix Server Manager software is not installed on the host or not working properly.
Resolution: Install or re-install vMatrix Server Manager.
2) The host or the zero clients are not connected to the LAN.
Resolution: Connect both the host and the zero clients to the LAN, and make sure the network is fine.
3) The zero client is with a new firmware version while the vMatrix Server Manager version on the host is out of date.
Resolution: Upgrade the vMatrix Server Manager.4) IP Addresses in the DHCP pool have been used up so that new connected zero clients cannot find hosts in the LAN while the old connected zero clients do not have the problem.
Resolution: Go to the DHCP setting page and enable more IP addresses or shorten the time of IP address tenancy.
06. Zero clients cannot connect to the selected host.(Last update: 23-May-2016)
Please resolve the issue according to the prompt if there is, if there is not, refer to the followings.
1) A pop-up window says that the device serial number is invalid.
Resolution: Contact our technical support team with series numbers.
2) unstable Local Area Network (LAN).
Resolution: Examine cable and switch and make sure the zero clients are connected to the host in the same LAN.
3) IP address pool is full that new devices cannot login.
Resolution: Lease more IP addresses, and recommend shorten IP address tenancy time in case there is a plenty of mobile devices connecting to the same network.
4) IP address conflict that the sign-in of one user may log the other out.
Resolution: Make sure all devices use different IP address from the others in the same LAN. Recommend using default DHCP instead static IP addresses.
07. Connecting USB devices to vCloudPoint zero client.(last update: 2018-1-5):
USB devices that are tested to work on the vCloudPoint zero clients:
Storage Devices, USB Hubs, Single, Multi-functional & Dot Matrix Printers,Smart Card Reader, Office &
POS Scanners, Single Touch Screens, U keys, Parallel to USB Converters, etc; An external power supply
may be required for devices working on large voltage.Click to download the list of tested USB devices ; other USB devices that are not listed but functions in the same way are supposed to be supported as well.
Using USB devices with vCloudPoint zero clients:
To use USB devices with vCloudPoint zero clients, you simply installed the native device driver on the host system as you normally do when using PCs. NO extra drivers are required for the zero clients. vCloudPoint USB redirection technology allows USB devices to work on the zero clients as well as on the host.
Printing devices and storage connected to shared host can be accessed by all client users. Printing devices connected to the zero client can be accessed by all other users but storage devices connected to the zero client can be accessed to the current user only due to vCloudPoint’s vCell User Isolation technology.
08. USB and audio drives cannot be installed in Windows10, 8.1, 8 & 7 Operating Systems without internet connection.(Last update: 11-Mar-2016)
In Windows 10, 8.1, 8, & 7 Operating Systems, all drivers and programs must be digitally signed (verified) in order to be installed. If you do not have internet connection for your first time of vMatrix Server software installation, you have to disable Windows Driver Signature Enforcement. Otherwise the USB and audio drivers cannot be executed for failure of getting signature verification.
Please follow these steps to disable Driver Signature Enforcement in Windows 10, Windows 8.1, Windows 8, Windows 7, Windows Server 2008 R2 once.
(Tip from http://www.wintips.org/how-to-fix-windows-cannot-verify-the-digital-signature-for-this-file-error-in-windows-8-7-vista/)
Step 1. Enter in Advanced Options menu.
To enter in Advanced Options menu in Windows 8 & 8.1 OS:
1. Press “Windows”
 + “R” keys to load the Run dialog box.
+ “R” keys to load the Run dialog box.2. Type “shutdown /r /o” and press Enter.
3. Windows informs you that you are about to be signed off. Press “Close”.
4. When Windows restarts, press “Troubleshoot” .
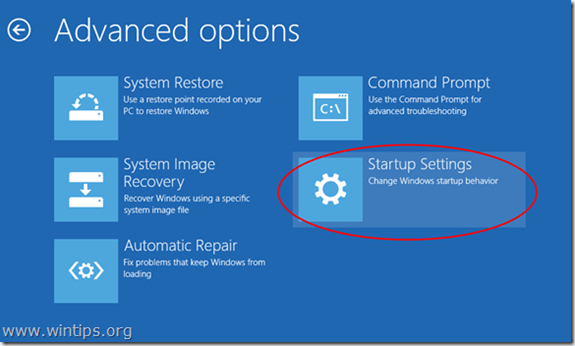
5. In the “Troubleshoot options” screen, choose “Advanced options”.
6. In the “Advanced Options” window, choose “Startup Settings”.
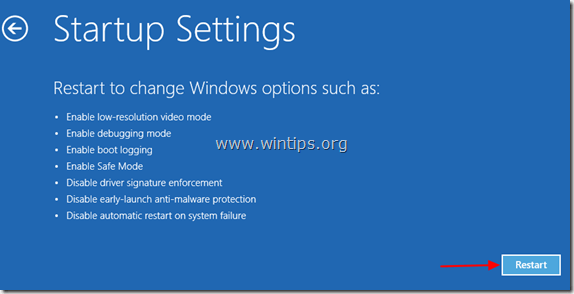
7. In “Startup Settings” screen, click “Restart”.
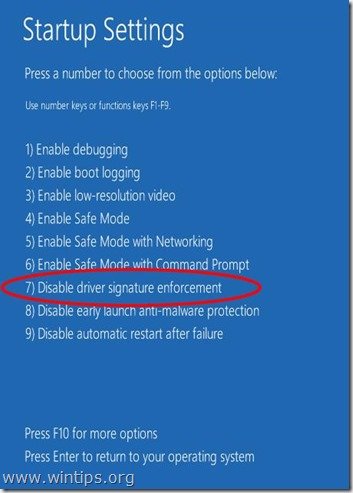
8. After restart in “Startup Settings” windows, press the “F7” (or the “7”) key on your keyboard to “Disable driver signature enforcement”.
Your computer will restart again.
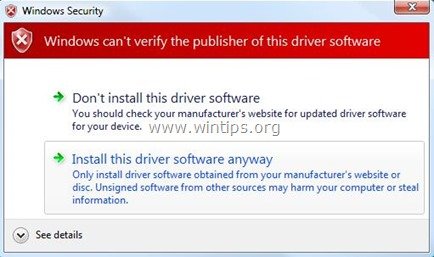
9. After the restart, proceed to install your unsigned driver. During the installation procedure, Windows will inform you that can’t verify the publisher of this driver software. At this point, ignore the warning message and choose “Install this driver software anyway” to complete the installation.
09. All USB devices, user audio cannot work and video performance is bad (cpaccel.exe error).(Last update: March-04-2016)
Why all USB devices, user audio cannot work or videos cannot be played smoothly?
If you have one or all of the above problems, you may probably see “cpaccel.exe” (Cloudpoint Multimedia Accelerator ) error message from Windows or by running vMatrix Diagnostic Tool. This is due to some file missing of vMatrix Server Manager, mainly caused by mistaken removal or block of fire-wall or anti-virus software. The best and quickest way to fix this problem is to re-install vMatrix Server Manager (make sure you have disabled security software before installation). If you still have this problem in use, you may have to add vMatrix files or ports to exception list of security software. Also refer to How to Configure Firewall and Antivirus software for vCloudPoint Products on this page.
10. Application compatibility in the multi-user environment.(Last update: Sep-13-2016)
What software can or cannot be run on vCloudPoint zero clients?
1, Most popular Windows software can be run with vCloudPoint zero clients such as Office Applications, Skype, Outlook, Chrome, Firefox, IE, Edge, Teamviewer, Adobe Photoshop, Adobe Illustrator, Adobe After Effects, Adobe Indesign, AutoDesk CAD, and Camtasia, etc.
2, 3D games are not supported. 3D design software like 3D Max can be run but rendering takes long time. Other 3D software may not be supported as graphic card is not utilized by the zero clients on processing. The experience of desktop on the zero client is just like that of the host computer without a discrete graphic card.
3, A few software cannot work in the multi-user environment.
Adobe Premiere and VPN are known to be not supported in the multi-user environment. To know if your desired software can be run in the multi-user environment without zero clients, you can try running the software in remote desktop sessions with PCs (run “mstsc”).Trouble-shooting some applications that are supposed to be supported but still cannot be run with vCloudPoint zero clients:
1, The disk partition where the applications are installed must be set to be visible to terminal users. To configure visible disk partitions, open vMatrix Server Manager, click Configuration, and then Storage Visibility, tick the partition where your applications are installed.
2, Try disabling or enabling Windows UAC. Some software, especially security or administration software, may requires administrator authority when Windows UAC is enabled. Therefore, when a non-administrator launch the software, it prompts the user to continue with administrator authority. In this case, you have to disable UAC for terminal users with ordinary user account level. While some software, especially the business software, like the famous Chinese software, Foxmail and Fangyou, were designed without considering multi-user environment that all user data are stored in the same folder, which leads to interference among the users. For these software, you need to enable Windows UAC so that data of each users will be redirected to different folders. And you may also have to install the software in the folder of program files or program files (x86) under the system partition (C:\).
3, Change installation directory to non-user based. Default installation directory of some software like Kingsoft WPS are user based, like “C:\Users\Administrator”. When installing, you must change it to non-user based one, such as “C:\Program files\” otherwise other users are not able to run this software.
11. Adding system created users to the vMatrix Server Remote Users group (Remote Desktop Users group)(Last update: 28-Mar-2018)
By default, the Remote Desktop Users group is not populated. You must decide which users and groups should have permission to log on remotely, and then manually add them to the group. Particularly with vCloudPoint: Users created with vMatrix Server Manager are automatically added to the Remote Desktop users group, but if the users are not created with vMatrix Server Manager, e.g., users created from system or domain, and they are non-administrators, then you have to manually added to the Remote Desktop users group.
- Open Computer Management. To open Computer Management, click Start, click Control Panel, double-click Administrative Tools, and then double-click Computer Management.
- In the console tree, click the Local Users and Groups node.
- In the details pane, double-click the Groups folder.
- Double-click Remote Desktop Users, and then click Add….
- On the Select Users dialog box, click Locations… to specify the search location
- Click Object Types… to specify the types of objects you want to search for.
- Click Check Names; When the name is located, click OK.
Important Note: To remotely log into the local system, the users must be in the Remote Desktop Users group, therefore, system created users or domain users must be manually added in the Remote Desktop Users group but NOT vMatrix Server Remote Users group.
12. Configuring firewall and antivirus software for vCloudPoint products.(Last update: 11-Mar-2016)
Configuring Firewall and Antivirus Software for vCloudPoint Products
Anti-virus, firewall, and other types of security software can sometimes interfere with the initial configuration or continued operation of vCloudPoint’s vMatrix software. This document gives basic information on applications, services, and network communication within vMatrix, which can be used to configure security software and help ensure compatibility and stable, continued operation.
vMatrix Installation
Please make sure to DISABLE any Anti-Virus or Firewall software during the installation of our product. Software of this type has been tested and known to interfere with the installation of our product. After installation has completed, you may re-enable Anti-Virus and Firewall software.
If system instability occurs after installing vMatrix, please try removing vMatrix and any anti virus or security software present, and then re-installing vMatrix. If the system is stable in this configuration, re-install the anti-virus software. In some cases, this change in install order can improve the interaction between vMatrix and anti-virus software. If issues persist, please try configuring your security software to ignore/allow/trust the following ports and executables:
Exceptions
1. Port Exceptions
Remote Desktop Services: TCP 3389
vMatrix Network Services: TCP 13389-13342 plus 3 per userUDP 13389
These ports are default settings on vMatrix’s installation but can be customized at vMatrix -> Configuration ->IP/TCP ports.
2. File Access Exceptions
On Firewall:
C:\Program Files\Cloudpoint\vMatrix\CpDaemon.exe
C:\Program Files\Cloudpoint\vMatrix\Driver\CpAccel.exeOn Anti-virus:
— By specific files:
—- For vMatrix functionality
C:\Program Files\Cloudpoint\vMatrix\CpDaemon.exe
C:\Program Files\Cloudpoint\vMatrix\Driver\CpAccel.exe—- For vMatrix tray icon and User functionality
C:\Program Files\Cloudpoint\vMatrix\CpDeploy.exe—- For vMatrix Admin manager
C:\Program Files\Cloudpoint\vMatrix\CpManager.exe—- For vMatrix Diagnostic tools
C:\Program Files\Cloudpoint\vMatrix\DiagnosticTools.exe—- For vMatrix Install and Update deploy tools
C:\Program Files\Cloudpoint\vMatrix\InstallDeployTools.exe— By folder:
—- For all vMatrix functionality
C:\Program Files\Cloudpoint\vMatrix13. Remote connecting vCloudPoint zero clients over WAN (cross internet).(Last update: 10th-May-2019)
For remote connection with vCloudPoint zero clients over WAN, setting DMZ host is the easiest way but unsafe, therefore, you can add these ports in your router instead.
The listen port for Remote Desktop Service itself also should be open. It uses TCP 3389.
The vMatrix Network Service uses both TCP and UDP ports. The broadcast port is fixed using UDP 13389, and the listen port takes 5 ports from 13389 to 13393 and 1 extra for each client user. The following example is given on 10 users (always reserve more ports if possible).-
- 3389- 3389 192.168.x.x TCP
- 13389- 13389 192.168.x.x UDP
- 13389-13403 192.168.x.x TCP
These ports are default settings on vMatrix installation but able to be customized at vMatrix -> Configuration ->IP/TCP ports.
Note: Due to the limited bandwidth and high latency of most cross-internet visits, the desktop performance may be significantly compromised. If you are planning to connect the zero clients in this approach permanently, please make sure both the client side and the host side have efficient internet condition for delivering desirable desktop performance .
14. Updating the zero client firmware.(Last update: May-23-2016)
It is always recommended to use the latest available version of firmware on your vCloudPoint zero client. Each installation of vMatrix Server Manager includes the latest firmware, so no additional downloads are necessary to complete this process. When powered on, the zero client establishes connection with vMatrix Server Manager and asks for update if there is a new version available for update.
15. Resetting the vCloudPoint zero clients.(Last update: May-23-2016)
vCloudPoint zero clients like S100 provide two different methods to reset the device configurations:
1. Resetting custom configurations — press F2 on device boot.
This is to wipe out custom configurations such as saved username, password, resolution, background image and network, etc. This is often used for restoring desktop resolution which is out of range of the monitor to 1027×768.
2. Resetting firmware — long press the switch button until you see the resetting window.
This is to reset the device firmware to the factory installed one. All configurations will be recovered to the factory defaults. This is often used when device system turns faulty or is damaged by improper firmware upgrade.
16. Connecting vCloudPoint zero clients to host through wireless network (WIFI).(last update: Jul-26-2016)
If you purchased a non-WIFI model of vCloudPoint zero clients, but later you want to work in the wireless environment, you can turn the zero client into a WIFi supported one by simply attaching a compatible external USB antenna to the vCloudPoint zero client. There are two ways for you to get the external USB antenna.
1, You can purchase the external USB antenna from your local vCloudPoint dealer.

2, Any antenna that is built with RTL8188EUS chip and connects with USB 2.0 standard is supported by vCloudPoint zero clients.
Given blow is the specification of the external USB antenna:
Connection USB2.0 Chip RTL8188EUS Antenna External 5dBi antenna Antenna standard IEEE 802.11g IEEE 802.11b IEEE 802.11n Speed 11b:1/2/5.5/11 Mbps 11g:6/9/12/18/24/36/48/54 Mbps 11n: up to 150 Mbps Distance up to 200 meters indoor Frequency range 2.4~2.4835GHZ Working channel 1~14 Security features WPA-PSK/WPA2-PSK WPA/WPA2 64/128/152bit WEP encryption Power 2.5W Steps to configure external WIFI:
1, attach the USB antenna to the zero client;
2, reboot the zero client;
3, go to the “Network” page and you will see the WIFI option coming. See pictures below.
(the WIFI option will automatically display on Network page once the WIFI module is detected on device boot.)
(the first picture shows the “Network” page without WIFI option, and the second one shows that with WIFI option.)
17. Enabling theme and wallpaper customization for zero client users.(last update: Aug-09-2016)
By default, theme and wallpaper customization is disabled for terminal users through remote desktop connections. Administrators can enable this option for terminal users through a few simple steps. But enabling this option will increase large resources consumption on the host.
Here are steps to enable theme and wallpaper customization on Windows:
1) for hosts running Windows Client Systems like XP, 7, 8, 8.1, 10 (Desktop Experience features of client systems are pre-installed on system installation).
Open vMatrix Server Manager, on the initial User Management page, right click on the user module and then select “Property” to enter the user’s personal settings. (If you are configuring for all users at a time, go to “Configurations” -> “Default User Settings”.)

Click on “Advanced” tag and then select “optimum” to enable all desktop experience options including wallpapers, themes, menu animations, and window content on dragging. To only enable a single desktop experience option like wallpapers or themes, you can click on a “custom” button for further customization.

Scroll down to “Desktop Options”, select the options which you like to enable, and apply.

The change will take effect on the user’s next login.
2) for hosts running Windows Server Systems like Server 2008R2, 2012, 2012R2, 2016 and Multipoint Server 2011, 2012 (Desktop Experience features for server systems are not installed on system installation).
For server systems, you have to install the Desktop Experience features before configuring at vMatrix Server Manager.
Open Windows Server Manager;

Click “Add roles and features”;

Search for Features –> Desktop Experience;

Confirm to install Desktop Experience features;

When completed, restart the system and then open vMatrix Server Manager to enable the Desktop Experience options as the same to configure for Windows Client Systems mentioned above.
18. Disable Pop-up Window Of Requesting Admin Permission (UAC whitelist)(last update: Mar-29-2018)
Disable Pop-up Window of Requesting Admin Permission on Running Some Applications by adding The Applications to The UAC Whitelist
Description:
For security and management concern, you are recommended to have UAC (User Account Control) enabled. But with UAC enabled, zero client users may be asked by the UAC to enter admin credetials when they are running some applications that require admin permission. In this case, you may add these applications to the UAC whiltelist without granting the zero client users with admin permission.Notes:
1) UAC whitelist is used only when UAC is enabled. Refer to the document of User Account Control to enable UAC.
2) This feature requires the installation of ApplicationCompatibilityToolkitSetup.Configuration Steps:
-
- Install exe. Simply click Next to finish installation.
-
- Open Compatibility Administrator(32-bit means adding a 32-bits application to the whitelist and 64-bit means adding a 64-bit application to the whitelist.
-
- Right click New Database, select Create New, select Application Fix…
-
- Enter the names of the application and the vendor to be fixed then click Browse.
-
- Find the installation path of the application, select the .exe launcher and click Open.
-
- Confirm and click Next.
-
- Check RunAsAdmin and RunAslnvoker, click Next.
-
- Click Next.
-
- Click finish.
-
- Click Save.
-
- Enter a DataBase name on the pop-up window, click OK.
-
- Enter a file name, then save.
-
- Click File then choose Install.
-
- The application now has been added to the UAC whitelist and zero client users can run the application without admin permission.
Download This Guide18. Fixing the problem of Windows system patch causing concurrent multi-user login failed.Issue:After installing the recent Windows system patch, shared hosts with RDP Wrapper does not support multiple user login. The system prompts a warning that the remote desktop user will log the previous user out. When running “RDPConf” file of RDP Wrapper, it shows “NOT SUPPORTED”.
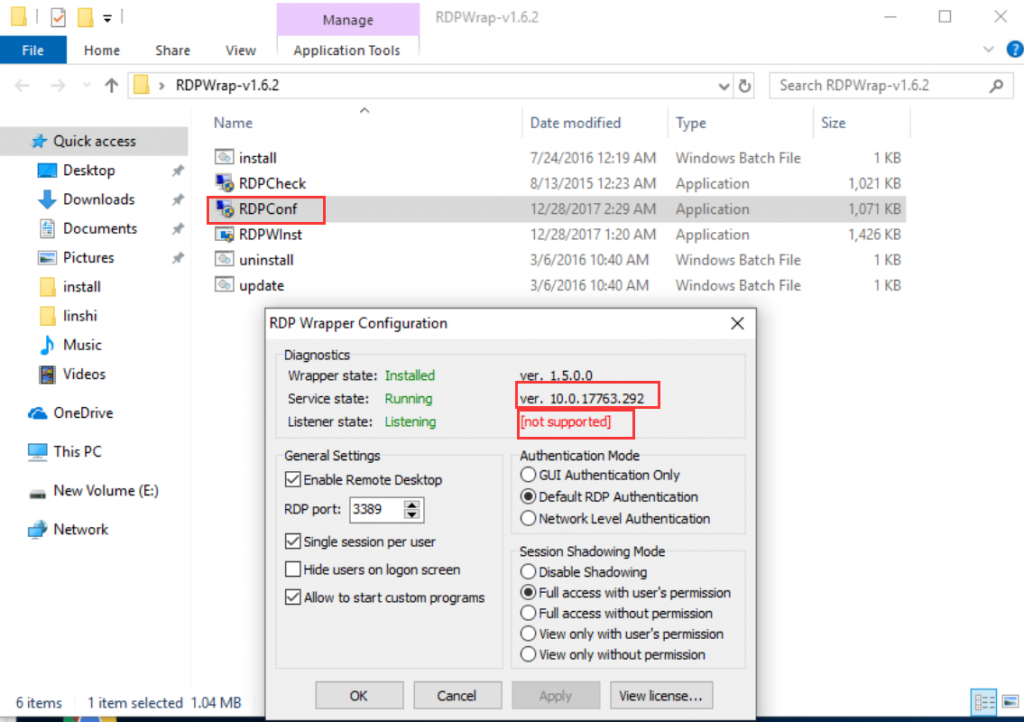
Cause:the system patch modified the terminal services (termsrv.dll) file, causing the RDP Wrapper failed.
Prior Solution: by updating RDP Wrapper
Run “update.bat” directly in the RDP Wrapper folder and wait for seconds for processing update; then run the “RDPConf.exe” file to check if it is supported after update.
If the above update does not work, try the following solutions.
Solution 1 [recommended][/recommended]:by replacing the terminal services file (termsrv.dll) with an old version.
- Uninstall RDP wrapper: run the “uninstall.bat” file at the RDP Wrapper’s folder.
- Stop remote desktop services: open “services” panel [run “services.msc”][/run] -> find “Remote Desktop Services” -> double click to disable it.
- Replace the “termsrv.dll” file:[click here to download and find the correct old version of “termsrv.dll” file according to your system][/<a]< div=””></a]<>
Go to C:\ Windows \ System32- >right click to choose”Property”->Security
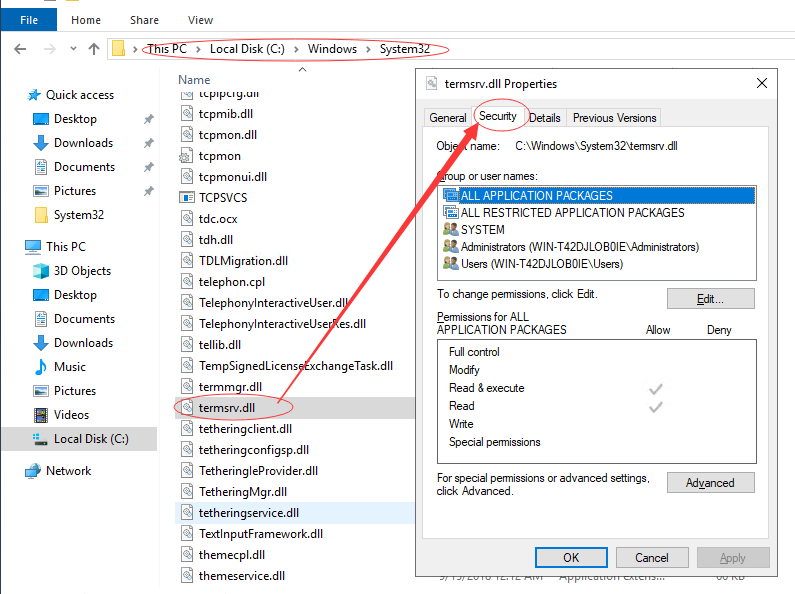
-> click “Advanced”
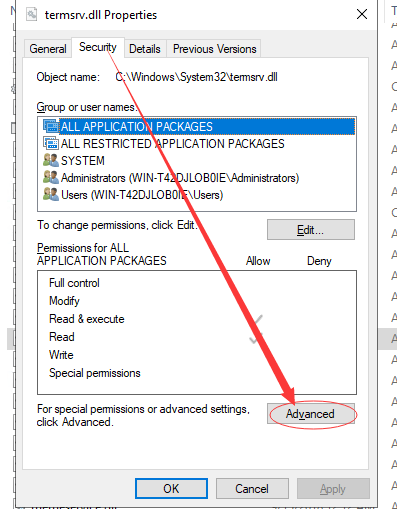
-> click “Change” to change the owner
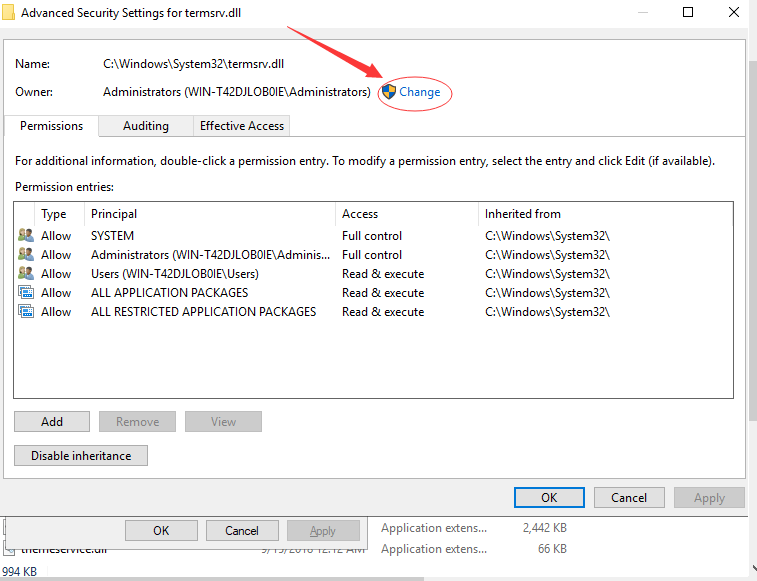
-> click “Advanced”
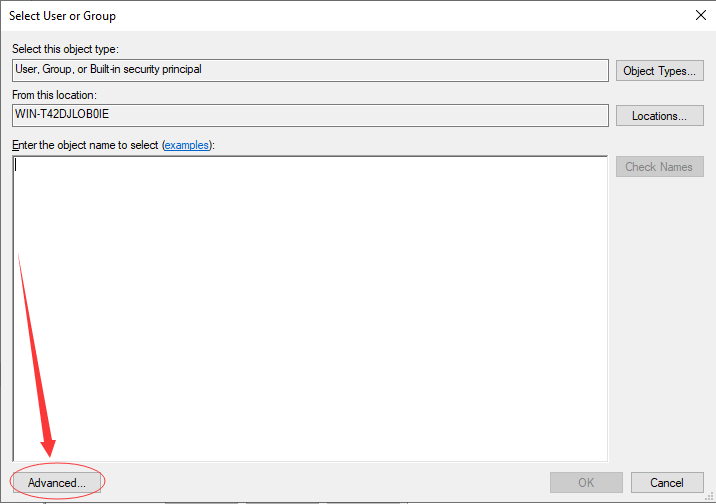
-> click “Find Now”
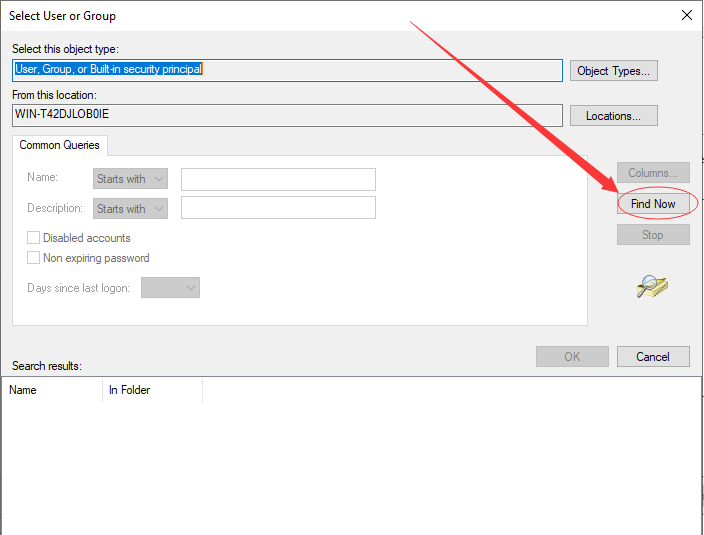
-> choose “Administrators” group
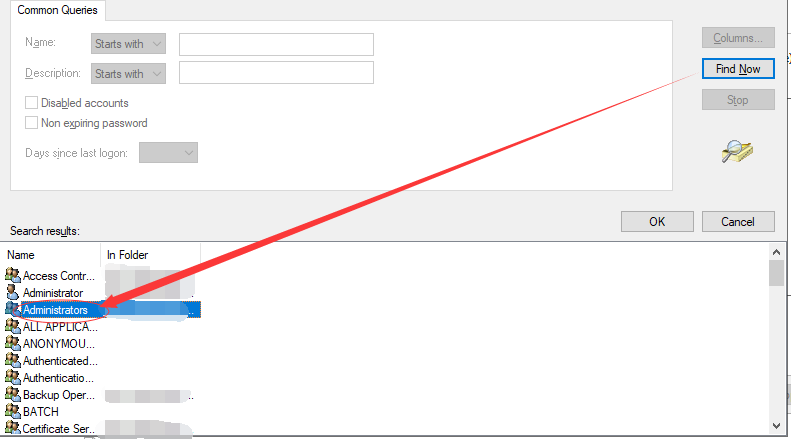
-> apply changes -> go back to “Security” tab, click “Edit…”
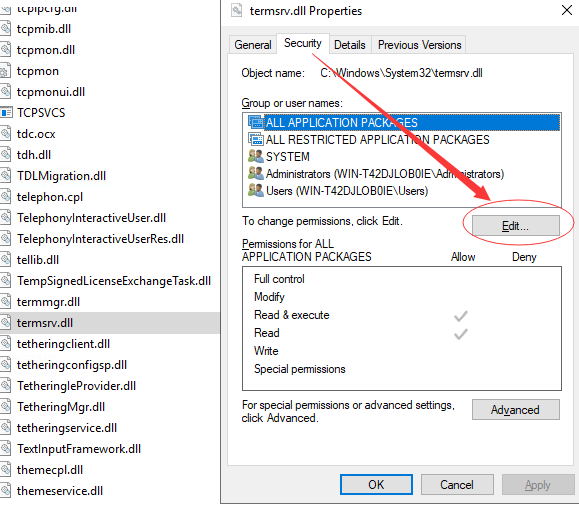
-> select to allow “modify”

-> apply changes -> right click “termsrv.dll” file, and rename it,e.g.: “termsrv.dll.bak”
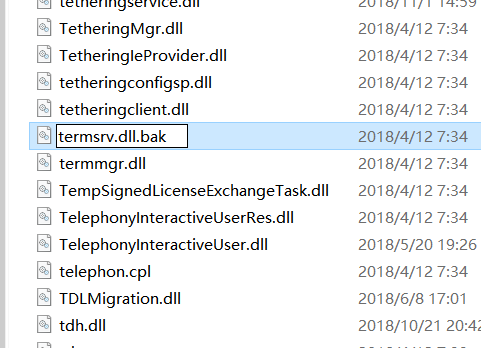
-> click “yes” in the pop-up window to confirm rename -> copy the downloaded old version of “termsrv.dll” into this folder to complete replacement.
- Enable remote desktop services.
- Re-install RDP Wrapper.
Solution 2:by uninstall the recent system patch.
Uninstall the patch through: start-> settings-> update & security-> view update history-> uninstall patches, click on the patch to uninstall; or run CMD command to uninstall: wusa /uninstall /kb:[patch code][/patch] /quiet .
Note: if you have deleted the patch backup in the system folder, you will find the uninstall option of this patch unavailable.
How to disable automatic system update?
Download and install Windows Update blocker at https://www.sordum.org/.
Windows Update Blocker is developed by BlueLife and publish on sordum.org. Windows Update Blocker is a freeware that helps you to completely disable or enable Automatic Updates on your Windows system, with just a click of the button.
Windows Update blocker helps you automatically disable or enable the system services in association with Windows update, including: Delivery Optimization Service(dosvc), Windows Update Medic Service(WaaSMedicSvc), Update Orchestrator Service(UsoSv), Background Intelligent Transfer Service(BITS). Or you can manually manage these services at the Services panel (run “services”).
Note: RDP Wrapper is developed by Stas‘M Corp and released on Github at https://github.com/stascorp/rdpwrap. Your use of RDP Wrapper is not legally licensed by Microsoft. We recommend you use RDP Wrapper for testing or trial purpose. For actual use of vCloudPoint products, your are always recommended to purchase and install Microsoft RDS-CALs which is compatible with any future Windows system updates.
For further assistance using vCloudPoint products, please email to [email protected].
-
-
Still Need Help?
Please email us with your question or issue. For technical problems, please describe in details with error messages, host environment such as system, vMatrix and device firmware versions, network condition, steps to re-generate the issues, recent changes you did that are suspected to be the cause of the problem and if possible, include screenshots in the attachment to help our support team analyse and bring up effective solutions.
-
Extensional Management Tips
Tip 01: Use VLC Player or K-lite codec pack to further reduce host CPU consumption on local video playback(last update: Jan-09-2017)
When a single host computer is shared by multiple users runnng vCloudPoint zero clients, how to make the most use of the host resources and support more users is the administrator’s top concern. Which media player you choose and how you use it for playing local videos has great impact on the CPU consumption of the host. GOM Player, KM Player, Potplayer, SMPlayer and Media Player Classic are some of the popular media players that customers are most likely to use. These media player have the most codecs included for supporting a large number of media formats. However, as some of these media players do not support hardware acceleration, you may experience heavy CPU consumption when playing local videos with them.
Strongly Recommended:
VLC player supporting client-rendering with hardware acceleration
To help customers offload host-side cpu consumption on video playing and support more video users per host especially for cases where simutaneous video play is often required, beginning from vMatrix 2.0 version, we introduced a new feature of client-rendering support. This feature allows local videos played on the zero client with VLC player to be rendered locally by the client processor instead of the host cpu, therefore, host CPU consumption is only taken by the running the VLC player itself to as low as less than 1% of an i7 processor per video. This feature is supported by VLC player of 2.1.5 or newer versions and works automatically after the installation of vMatrix 2.x. You just make sure you are using the correct versions of vMatrix and VLC player and VLC player is selected to play the video, then you are ready to “save”.Note: As the media content is not rendered at the host side, there is a drawback of using this feature: media content within the VLC player cannot be viewed by the administrator through monitoring at the host side.
Alternative:
Use K-lite codec pack with Media Player Classic supporting host-rendering with hardware acceleration
When using MPC (media player classic) for playing videos on the zero clients, although the rendering job still is done by the host CPU and the consumption is higher than using VLC player, as MPC supports hardware decoding, the host CPU consumption is greatly reduced, to as low as 1/2 of using other players without hardware acceleration.
Beblow is the download link and configuration steps:
1. download K-lite standard codec pack at http://www.codecguide.com. The Media Player Classic is bundled.
2. install the K-lite pack on the host. The Media Player Classic is integrated so you don’t have to install it separately.
3. Open “Codec Tweak Tool” at “Start” menu–>”K-Lite Codec Pack” or “Tools” at the installation file.
4. Click on “DirectShow (x86)” if you are Windows system is 32 bits, or “DirectShow (x64) if 64 bits.

5. On the next popup window, select “Video: LAV Video Decoder”, and apply.

After it is applied, “LAV Video Decoder” goes to “DISABLED FILTERS” as below:

6. Open the Media Player Classic, go to “View”-”Options”-”Playback”-”Output”, select the “DirectShow Video” option. And all configuartions complete.
 Tip 02: Use Network-Attached Storage (NAS) As Primary Storage For User Data
Tip 02: Use Network-Attached Storage (NAS) As Primary Storage For User Data(last update: Mar-29-2018)
About NAS
NAS : Network-Attached Storage is a file-level computer data storage server connected to a computer Network providing data access to a heterogeneous group of client.NAS(Network-Attached Storage) can be integrated into vCloudPoint’s shared computing solution to allocate private storage for each assigned zero client User.
Synology Network Storage Installation And User Instructions
Notes:
- This installation guide only applies to NAS model DS216j used as users’ private disk. Please choose the appropriate network storage plan according to your actual needs.
- Please use Gigabit or above LAN to ensure NAS Network bandwidth.
- Please use LAN with DHCP that can automatically assign IP.
- To use the other functions of Sysnology NAS, please refer to Synology’s official website :https://www.synology.com
Hardware Models:
NAS Server: Synology DiskStation DS216j
Hard Disk: Western Digital NAS Red Disk 4TB * 2
Hardware setup:
- Install the hard drive into the NAS, and secure it with screws.
- Connect the NAS to the switch using Ethernet cable.
- Connect the NAS to the power and finish the setup.
First Time Installation:
- Power the NAS device on, and wait for 1 to 2 minutes.
- Open the browser with any computer in the same LAN, view http://find.synology.com or the IP address of the NAS device to enter the Web Assistant page.
- After entering the Web Assistant page, click Install Now and confirm the hard disk mode (select the default system) to download the Synology DSM system from internet, follow the prompts to complete the installation.
- After installing the system, create the administrator account and customize DSM update and maintenance; leave QuickConnect settings as default.
- After initial installation is complete, enter the system;this storage solution is used only as a private disk for vCloudPoint users, other plug-ins is not required for installation.
NAS System Quick Setup:
- Open the control panel -> file sharing à shared folders and edit homes
- Select: (Hide this shared folder in “My Network Places”; Hide sub-folders and files from users without permission; Enable recycle bin) Cancel: (Restrict access to administrator only)
- Confirm the settings of the homes
- Apply the same steps to rest of the Shared Folders.
- Open Connectivity-> Network -> Network Interface, select LAN and Edit:
- IPv4 -> Usemanual configuration, set static IP address for the NAS device;
- IPv6 -> Select Off to turn off the IPv6, then confirm the
- Open Connectivity-> network -> traffic control, select the top right corner of the LAN -> Click Edit -> select All ports, Set the bandwidth settings. The default NAS LAN transmission bandwidth is 1 Gbps. But we recommend to set to 20000KB/s, the largest 40000KB/s. If bandwidth limitation is not set, users will use up all the bandwidth while transferring files.
- Open System-> theme style, set page landing page title and theme as needed.
- Open System-> Hardware & Power …you can customize Power Recovery, Beep Control, Fan Speed mode, Led Brightness Control.
- Open File sharing-> User -> Advanced : Password Settings-> apply password strength rule, scroll down to User home -> Enable User home services and Recycle bin.
- Open File Sharing -> User accounts, create users.
- Enter the user name and password (we recommend that NAS password should be different from vCloudPoint User password), Next step.
- System default group: leave as default, Next step.
- Assign shared folder permissions: leave as default, Next step.
- User quotas setting: set it according to the actual use of each user and can set to limit or unlimited, Next step.
- Assign application permission: leave as default, Next step.
- User speed limit: leave as default Next step.
- Check the new user settings, confirm then Apply.
- Select the user just created, select user -> Create-> Copy User, simply enter the user name and password, and copy all the user configuration.
- NAS installation completed.
Connect to the NAS device on a zero client:
- Open the File Explorer, enter the NAS device’s IP address : \\ xxx.xxx.xxx.xxx.
- Enter the assigned NAS user name and password, press OK.
- Right-click the home folder, select Map Network Drive, click Finish.
Tip 03: Restrict Users from Running Specific Applications(last update: Mar-29-2018)
Software Restriction for Zero Client Users by Using AppLocker Group Policy
Description:
AppLocker Group Policy for Windows system Applications can be used for restricting User or User Groups from running and installing programs.Typically, only administrators have the permission to install programs. But green software and other software package do not necessarily need administrators’ permission to be installed. So using AppLocker Group policy can directly limit the User from accessing and installing all programs.
Tips:
- AppLocker Group Policy needs to be used in conjunction with User Account Control (UAC). Please refer to User Account Control Guide to turn on UAC.
- Before setting up AppLocker, please standardize the program installation path, be sure to install the required programs in C: \ Program Files or C: \ Program Files (x86) path. As Program Files folder is a kind of system file, which requires the administrator permission to make changes.
- Recommended operating systems: Windows 7 (Ultimate, Enterprise), Windows 8.1 Enterprise, Windows 10 (Professional, Enterprise), Server 2008R2 Standard, Datacenter, Server 2012R2 (Standard, Datacenter), Server 2016 (Standard, Datacenter).
Quick Configuration Steps:
- Enter Service, set the Application Identity startup type to automatic
- Enter the local Group Policy Editor àAppLocker
- Executable rulesà Windows installer rulesà and script specifications create default rules
- AppLocker open Configuration rules
- Restart the host, Then the AppLocker settings will take effect.
Tip 04: Restrict Users To Modify System Files & Settings(UAC)(last update: Mar-29-2018)
Restrict Zero Client Users To Modify System Files & Setting By Using User Account Control (UAC)
Description:
User Account Control (UAC) is a new set of infrastructure technologies in Windows Vista (and later Microsoft operating systems) that helps prevent malicious programs from damaging your system and helps organizations deploy easier-to-manage platforms.With UAC, applications and tasks always run in the security context of a non- admin administrator account, except when an administrator specifically grants administrator-level access to the system. UAC will prevent the automatic installation of unauthorized applications to prevent inadvertent changes to the system settings can effectively limit the zero client user to modify the system.
Tips:
-
- Administrators must use a complex password.
- Do not add zero client users to the administrator group as UAC restrictions do not apply to administrators.
- After enabling UAC, when a nornal user attempts to open a folder that needs admin permission, he will be asked to enter the admin password. IT admins are suggested not to grant a normal user with admin-level access to temporarily access a restricted folder. Because once it is done, the normal user will have permanent access to this folder.
- UAC is recommened to be used with C Drive Access Restriction. For more detalis, please refer to the document of Restrict User Access To C Drive.
- Note: UAC is enabled by default in certain Windows Systems.
Enabling UAC:
- Open control panel, click User Account and Family Safety.
- Click User Account.
- Click Change User Account Control Settings.
- Adjust the level to the third level or the highest level and click OK.
- UAC settings are completed; restart the host.
Tip 05: Restrict Users To Access C Drive(last update: Mar-29-2018)
Restrict Users Access To C Drive through Group Policy
Note:
- You can configure the Group Policy to prevent access to C drive through system File Manager, but you cannot restrict access through third-party file manager, for example, decompression software.
- After you restrict access to C drive by Group Policy, all users, including the Admin account, cannot access C drive. Therefore, before you configure the Group Policy, you shall complete all installations and settings in C drive.
- Although the default desktop file path is in C drive. (C \ Users \username \ Desktop), after the restriction configuration, users can still create, download or drag files onto the desktop, but the “paste” function on desktop is disabled. If you want to re-visit C drive, just modify the related Group Policy setting back to the default.
- When you configure C drive access restriction, you are suggested to have UAC enabled, otherwise, users are able to modify Group Policy to re-gain C drive access. For more details about UAC, refer to the “User Account Control” guide.
- Configuration Steps:
Log into the host with the Administrator account, run “gpedit.msc” to open the Group Policy Editor. - Computer Configuration>> User Configuration >>Administrative Template>>Windows Components>>Windows Explorer>> Prevent access to drives from My computer>> Edit policy setting.
- Enable this setting and select “Restrict C drive only” , click “OK“.
Tip 06: Limit User’s Disk Usage(last update: Mar-29-2018)
Limit User’s Disk Usage By Setting Disk Quotas
Description:
Disk quotas are applied to specific users and limit the amount of disk space that user can use on a particular volume.Quick Configuration Steps:
1) Enter Local Group Policy Editor, enable disk quotas..
2) Set Quotas for users at the Properties of the disk partition.
3) Restart the host.Detailed Configuration Steps:
1) Log in the host with an Admin account, run gpedit.msc to open Group Policy Editor.2) Computer Configuration->Administrative Template->System->Disk Quotas-> double click Enable disk quotas to open Disk Quota settings.
3) Select the Enable option, click OK to save the setting.
4) Open My Computer, select the disk partition you want to limit usage. In this guide we take Private Disk (E:) as an example. Right click and select Properties.
5) Select the Quota option, tick Enable quota management and Deny disk space user to users exceeding quota limit, select and enter the same number for Limit the disk space and warning level.
Note:This operation only applies to the newly created user, you shall further do some configurations for the created users.
The option of Deny disk space to users exceeding quota limit shall be selected, otherwise, only a reminder will be shown but no restriction will be taken when a user exceeds the available space.
If you have not created users,you can skip the following steps. If you have created users, you shall still configure Quota Entries.
6) Click on the Quota Entries… option of the quota page of the previous step.
7) Select Quota in the task bar to create new quota entry. Click Advance.
8) Click Find Now, search for all the local users created, select and click OK to save.
9) Confirm the selected users and click OK.
10) Quota Entry windows will pop up. Enter the number for disk space and warming level, then click OK.
11) Log in with a created user, from the File Explorer, you will see the the disk partition size is limited to the number you just set.
Download This GuideTip 07: Prevent users from shutting down the host on Window 7 or XP(last update: Mar-29-2016)
On Windows 8 or later systems, remote desktop users are not able to shutdown the host. But for Windows 7 and earlier systems, the shutdown option is available to remote desktop users. Below is the guide to preventing zero clients users from shutting down the host.
1) on the host, open the security setting console through Control Panel –> Management Tools — >Local Security Settings –> Security Setting –> Local –> User’s right assignment –> Shutdown Operation system
2) delete users or groups that are not allow to shutdown host.
 Tip 08: Allow Zero Client Users To Shutdown The Shared Host
Tip 08: Allow Zero Client Users To Shutdown The Shared Host(last update: Mar-29-2018)
Allow Zero Client Users To Shutdown The Shared Host Through Group Policy
Description:
By the default Windows Group Policy settings, zero client users can not restart/ shutdown the shared host. But in some cases, you may want to allow some zero client users to shutdown the shared host when the IT admin is absent. In this case, you may configure the Goup Policy to allow some zero clients users to shutdown the shared host.Notes:
-
- IT admin shall remind zero client users to confirm if all other users on the same host are safely signed off before the shutdown/ restart operation. Zero client users can check out the connection status of all users on the host system at the User tab ofthe Task Manager (shortcut keys: Ctrl + Shift + Esc).
-
- To prevent from data loss or shutdown/ restart failure, zero client users shall save files, close applications and then sign off from the system before they power off the zero client device to end the work of the day.
Configuration Steps:
-
- Login to the system with an admin account,open the control panel.
-
- Open administrative Tools.
-
- Open Local Security Policy.
-
- Click Security Settings->Local Policy->User rights assignment, select shut down the system.
-
- Right-click System, set Properties, click Add Users or Group….
-
- Change the object type.
-
- Select Groups, confirm OK.Note: if you only want some specific users instead of all users to have the permission, you shall select the option of Users.
-
- Select Advance ….
-
- Click Find Now, select the group of vMatrixServerRemoteUsers, confirm OK.Note: if you only want some specific users instead of all users to have the permission and have selected the option of Users from the above step, you will be asked to select specific users here.
-
- Confirm the group or users are selected, click OK.
-
- Confirm that you have added the vMatrixServerRemoteUser group or users.
-
- All configurations are done.
Download This GuideTip 09: Disable Password Complexity Requirement On Windows Server Systems(last update: May-3nd-2018)
Disable Password Complexity Requirement on Windows Server Systems through Group Policy
Description:
By default, Microsoft Windows Server System enforces users to use strong passwords for safety. But you can disable password complexity through group policy through group policy to avoid the trouble of using complex password for zero client users.
Environment for this guide:
Windows Server 2012 R2
1, Click “Start” menu on the lower right corner of your desktop, and then go to “Run”, Input “secpol.msc” (without quotations). Then it appears the box of the Local Security Policy settings under the Group Policy.

2, Hit “Account Policy” on the right panel.

3, Hit “Password Policy”.

4, Find in the box “Password must meet complexity requirements”, and then double click it to change the setting.

5, In the pop-up window, select “Disable” and click “OK” to apply.

6, Now you can set new simple passwords. If needed, you can also disable password age, length and history in the same box.
Download This Guide -
To Better Use vCloudPoint
These guides demonstrate possible approaches to extend the functionality of vCloudPoint’s shared computing solution only. UAC, Group Policy and other Windows components belong to Microsoft. Other software or hardware mentioned here belong to their respective owners. For actual application of the 3rd party products, please refer to the related documents by their owners.
-
Knowledge Base
The configuration of a zero client itself does not contribute to the desktop performanceMost customers mistakenly think that a zero client should be, like thin clients, configured high in its internal hardware such as, CPU, flash, network chipset, to grantee a high performance.
Unlike x86 thin clients that are typically required for standalone usage and have local system and software. Zero clients offer nothing locally but just enable users to connect to a remote desktop. In other words, the residing hardware of a zero client do not act on jobs of processing locally as in thin clients, but only to initialize a conversation with the network, begin network protocol processes, and display desktop output. Therefore, the configuration of a zero client itself does not contribute to its performance. Even a zero client with powerful configuration as a Pro PC can’t guarantee good performance.
Then what helps with good performance to a zero client?
There are a few aspects
- Well-configured host computer– including sufficient cores and frequency of CPU, IOPS and stroage of Disks, size and frequency of Memory. (Multi-threading technology of Intel also helps increasing CPU capability and i series with hardware acceleration performs better than Xeon series of the same level. Disks in RAID configuration increases redundancy and performance. Intensive graphics processing requires sufficient frequency of memory. Video card on the host helps in video playback only.)
- Low latency, high-bandwidth network– recommend local-area network connections provided by standard 100 /1000 Mb/sec networks (i.e. Ethernet) between the host computers and the zero clients.
- High efficient remote display protocol– offers high-resolution sessions, multimedia stream remoting, dynamic object compression, USB redirection, drive mapping and more.
Of the above 3 aspects, only the display protocol is determined by the zero clients. The display protocol determines two critical measures: experience and resource usage. The sticking point for many organizations will be various levels of multimedia support. Regardless of implementation status, any organization can have issues with multimedia support. This is true not only in large implementations that push bandwidth limits — even smaller installations may consume enough bandwidth to push the limits of the display protocol without a bottleneck on the wire. vCloudPoint zero clients utilized our innovative DDP (Dynamic Desktop Protocol) for remote desktop display. This protocol is purpose-built for zero clients and is designed to make efficient use of the network bandwidth and host resources, delivering a user experience that is equivalent to or even better than a business PC.
(By vCloudPoint)
Network has a great impact on zero client performanceWe all know the zero clients are free of CPU, memory, processor and hardware requirements. This means that another strong factor plays a role in transmitting of the information from server to client. That is the network. And in case of zero clients, this network bandwidth should be really wide and sufficient enough for the seamless transfer of information.
Let us start with an example. S100 zero client uses Ethernet as the network connection. The deployment so far has registered recognition about its appreciable performance, which is attained with the category 5 or 6 network cable to connect to the Ethernet network. The next question is:
What is a Category-5 or Category-6 cable??
Usually, the high quality copper wires are used for Cat-5/ 6 cabling. They are twisted into 4 pairs which run along an outer cover. This design of the cable makes it immune to the other signal interferences, which means a better transmission of the data signal over the cable.
Most of the times, the poor cabling is responsible for the faulty network transmission. This very often leads to the unnecessary testing of the other equipments. There are a few very high standards tagged with the category 5 and 6 cabling, which must be followed during installation as well. This guarantees a high performance over the network.
Recommendation With Us:
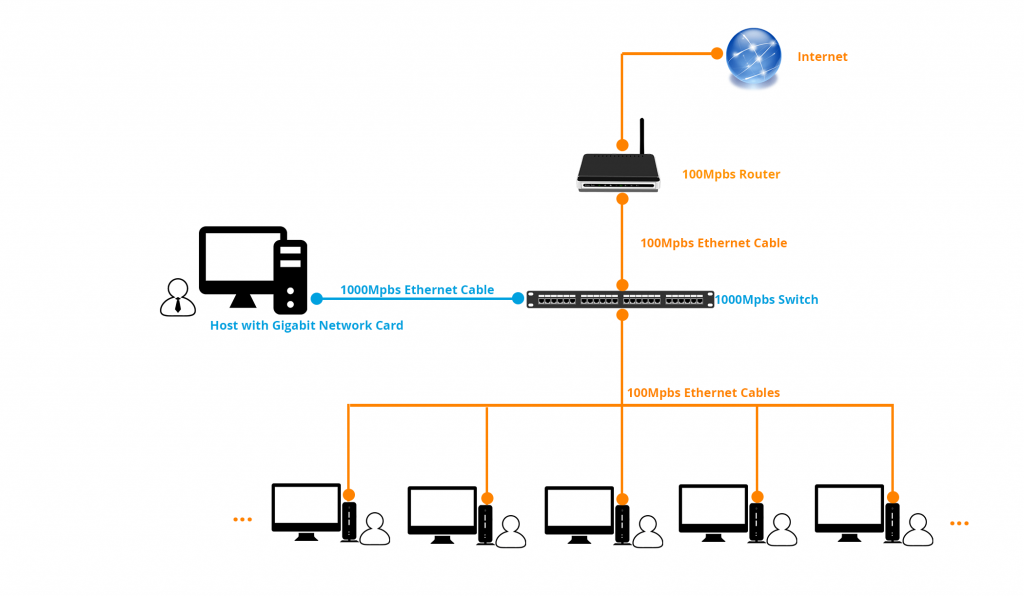
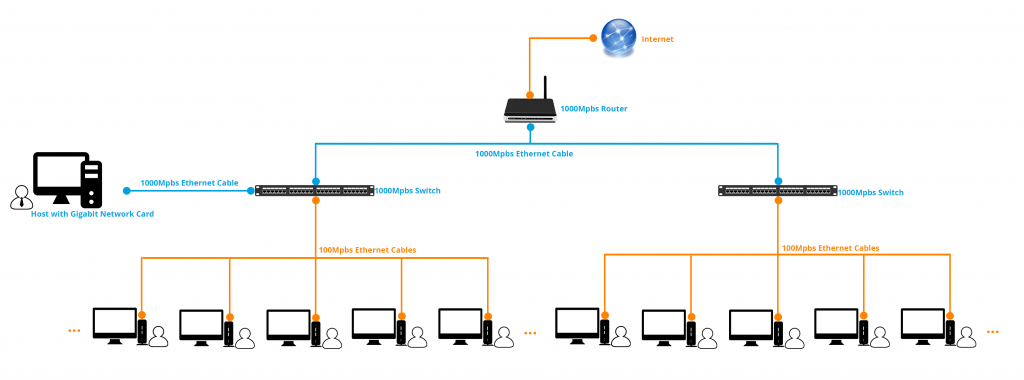
For multimedia intensive environments, especially those with concurrent multiple video playback, we recommend a standard 100 /1000 Mbps network between the host computer and the zero clients, to guarantee a smooth high-end experience; as shown in the figures: (click to view large pictures)
The videos consume higher bandwidth, for example, when the server side videos are played at vCloudPoint zero clients, each 480p video file consumes up to 13 Mpbs of the network bandwidth, a 720p video can take up to 15 Mpbs of bandwidth and a 1080p video can take up to 17 Mpbs of bandwidth straight away.
Most of the Wide Area Networks (WAN) have excessive latency and lower bandwidth. This compromises with the rich PC-like experience over the network.
The ideal recommendation from vCloudPoint is a low latency higher bandwidth Local Area Network, which is the secret behind the excellent performance of zero client devices.
(By vCloudPoint)
Get the skinny on zero clients vs. thin clientsThin clients used to be the thinnest, but now zero clients are giving them a run for their money with almost no storage or configuration requirements.
Zero clients are similar to thin clients in their purpose — accessing a desktop in a data center — but zero clients require a lot less configuration.
Zero clients tend to be small and simple devices with a standard set of features that support most users. They also tend to be dedicated to one data center desktop product and remote display protocol. Typically, configuration is simple with a couple dozen settings at the most, compared to the thousands of settings in a desktop operating system. Zero clients load their simple configuration from the network every time they are powered on, which means the zero clients at a site will all be the same.
Zero clients support access to a variety of desktop types, terminal services, a virtual desktop infrastructure or dedicated rackmount or blade workstations.
Zero clients vs. thin clients
The basic premise of a zero client is that the device on the user’s desk doesn’t have any persistent configuration. Instead, it learns how to provide access to the desktop from the network every time it starts up. This gives a lot of operational benefits because the zero client devices are never unique. This contrasts with a thin client, which may have local applications installed and will hold its configuration on persistent storage in the device.
The original thin clients were much like what we now call zero clients. They were simple devices that gave access to a desktop in a data center. Two factors led to the evolution of thin clients into thicker devices. The first was PC makers’ entry into the thin client market, and the second was a need to work around the limitations of remotely displaying a Windows desktop.
A brief history of thin clients
Thin clients became a mainstream product class shortly after Microsoft introduced Windows Terminal Server and Citrix launched MetaFrame, both in 1998. To enter this market, PC manufacturers cut down their desktop hardware platforms. They repurposed their PC management tools, reusing as much technology as possible from their existing PC businesses. This meant that a fairly customized Windows or Linux setup could become a thin client. But even a customized Linux build usually has local configuration and a fair bit of storage. As a result, these thin clients were not so thin, and their management tools could be relatively complex.
The other motivation to thicken clients was the need to handle rich media, such as video. Early remote display protocols didn’t produce great results, so technologies for thin client video rendering appeared. These used media players on the thin client rather than in the desktop, transferring the compressed video stream over the network. Now the thin client needed video codecs as well as a local operating system.
Over time, optional features for USB redirection, a local Web browser, Voice over IP integration agents and multi-monitor display support were added. Each additional feature increased the configuration and complexity of the thin client. After a few years, thin clients turned into small PCs. Some even added PCI or PC Card slots.
These thicker thin clients get quite close to a full PC in terms of capabilities and complexity. Instead of simplifying management, the thin clients forced IT administrators to manage the device on the user’s desk as well as in the data center. This is obviously not what we had in mind. Zero clients are a return to the simpler devices on user’s desks with simpler management.
Operational and security benefits of zero clients vs. thin clients
Any worker can use any zero client because the zero client doesn’t store anything unique. This gives workers the flexibility to access their desktops from any zero client anywhere in the organization, reducing the need for employees to carry laptops between branch offices or shared desks. An organization can simply provide desks with zero clients, with all uniqueness stored in the data center desktop.
Another benefit is that a new zero client can be shipped directly to the user. There’s no need for desk-side support or preconfiguration. All the zero client needs is a network connection and a power source. For an organization with many branch offices, this simplicity saves time and makes it considerably easier to set up a new hire or support a worker whose device is failing. Companies can even keep a spare zero client at each branch, which eliminates shipping delays.
Zero clients usually load their configuration from the network, often from a few files and shared by every zero client at a site. Changing a configuration generally means changing these shared files and then rebooting the zero clients. Updating zero clients is generally the same process: Place a new firmware file alongside the configuration files and reboot the zero clients. The new firmware is automatically loaded when the zero client boots. This makes it fairly simple to keep zero client builds consistent, so long as users turn off their zero clients at the end of the day.
One common reason to deploy data-center-based desktops is to contain data so a company’s intellectual property isn’t distributed to every desk. Because zero clients usually have almost no persistent storage, there is far less chance of critical data remaining on the device. Also, the zero client doesn’t run a general purpose operating system, so it’s unlikely to be compromised by a virus or network intrusion. In fact, this lack of local storage is a deciding factor for deploying zero clients in some highly secured environments.
Zero clients provide these benefits without the intrusion of a local operating system. For example, users don’t want to see how the client device handles the USB key they just plugged in — only their desktop should care. With thin clients, however, a local operating system must identify and handle the USB device before handing it over to the remote display client and then the user’s desktop. Besides this being a slow process, there’s an increased chance that something along the way will fail. Zero clients simply hand the USB device directly to the desktop, resulting in a far more PC-like experience. Zero clients also tend to show a far leaner local interface, getting to the user’s desktop with fewer dialogue boxes than thin clients.
(This was last published in April 2014 by Alastair Cooke on searchvirtualdesktop.techtarget.com)
Zero client vs. thin client computing: Why zero clients are betterZero clients and thin clients both offer virtual desktop access, but they aren’t the same when it comes to performance and scalability.
A zero client is similar to a thin client in that both provide access to virtual desktops, but they have significant differences when it comes to performance, usability and security.
A zero client is a lightweight appliance that gives the user access to a desktop stored in a data center. A thin client is more like a small PC, with few expansion options. It too can be a portal to a desktop in a data center, but it can also bring a lot of complexity.
Zero client vs. thin client computing: Plug and play
Zero clients provide the most PC-like experience for virtual desktop infrastructure (VDI). One example has to do with USB plug-and-play. When using a PC or thin client with a local operating system, there are three plug-and-play cycles when you plug in a USB device:
Local device plug-and-play. Device detection and driver installation for the USB device
VDI client overtake. Replacing the local operating system driver with a redirection driver
Remote plug-and-play (inside the virtual desktop). Device detection and driver installation for the USB device
It can take a while, sometimes minutes, from the time you plug in the USB key until it shows up as a recognized device. Usually, the first two plug-and-play actions aren’t visible to the user, so they give up in frustration and remove the USB key before the third stage begins.With a zero client, however, there should be no local plug-and-play. The whole USB experience is transferred to the virtual desktop in the data center. Only the remote plug-and-play inside that desktop occurs, and the user can see it, so the user knows to wait for it to finish.
Zero client vs. thin client performance and manageability
Zero clients tend to offer high performance. They should be well optimized for one VDI protocol and provide a great user experience with fast, smooth scrolling and the best video playback the network will allow. User experience is the defining factor in VDI success, so it is critical to use a device optimized for the VDI protocol. Zero clients usually provide the best display performance for the protocol.
Zero clients tend to be much simpler to manage, configure and update. Zero client firmware images are a few megabytes in size, compared with the multiple gigabytes that thin client operating systems take up. The update process is much quicker and less intrusive on a zero client than on a thin client, possibly occurring every day when the zero client boots. Thin clients need to be patched and updated as often as the desktop operating system they carry, but zero clients have no operating system, so they need fewer updates.
Zero clients have few knobs and switches to turn — probably fewer than 100 configuration items in total — so they are simple to manage. Often, their bulk management is a couple of text files on a network share somewhere. Thin clients have a whole operating system to manage, with tens of thousands of settings necessitating complex management applications, usually on dedicated servers at multiple sites.
A zero client is like a toaster: A consumer can take it out of its packaging and make it work. If the consumer is your staff at a remote branch, then there are a lot benefits to having them be able to do the deployment of a new terminal.
Sometimes, thin clients need special builds or customized settings applied to them before they are deployed — not ideal for rapid deployment. The ability to rapidly scale can be important when it comes to something like opening a call center to accommodate an advertising campaign or a natural disaster response.
Another advantage of zero clients is their lower power consumption. Thin clients have mainstream CPUs and often graphics processing units, but a zero client usually has a low-power CPU (or none at all), which cuts down on power consumption and heat generation. The simplicity of zero clients also makes for a much smaller attack surface, so placing them in less trusted networks is not so worrying. Also, placing them in physically hostile locations is safe; lower power and usually passive cooling mean that heat, dust and vibration are less likely to cause maintenance problems.
Zero clients are all the same. Models aren’t released every few months, but every couple of years, so your fleet will contain fewer different models. That means there’s no need for help desk calls to move a device from one desk to another, plus a much more consistent user experience. Your supplier’s inventory of zero clients will also have fewer models, which should lead to better availability when you need new zero clients.
(This was last published in April 2014 by Alastair Cooke on searchvirtualdesktop.techtarget.com)
-
Learn The Technology Behind
These articles are either written by vCloudPoint staff or picked up from the internet in an objective perspective to help you easily and correctly learn this technology and industry behind, so as to help you make better purchase decision.